– Using the CVE-2021-26855 Payload
After the recent vulnerabilities that hit Exchange Servers On-premises I found sometime to install KaliLinux and try to check what kind of information would I get from the patched servers.
I downloaded the payloads and tried to run it against couple of clients that I have patched the servers for luckily no authentication was made.
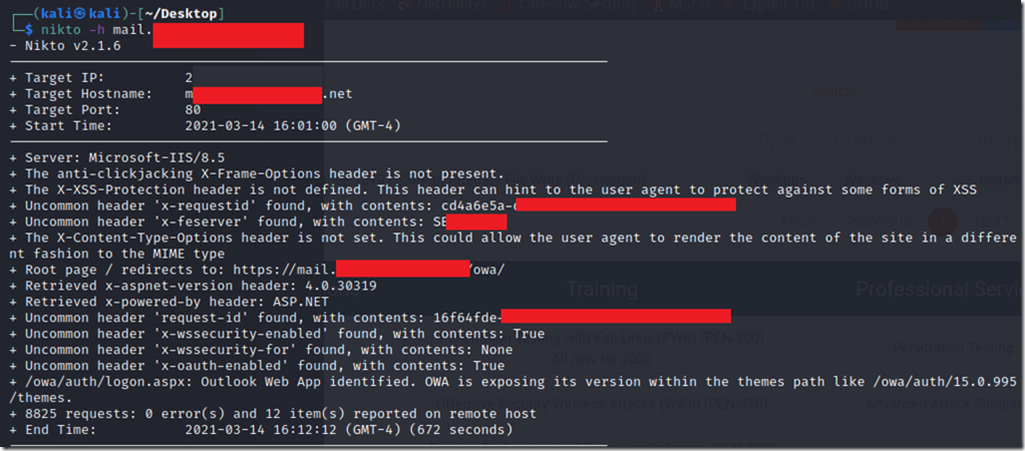
– Using Nikto scanner
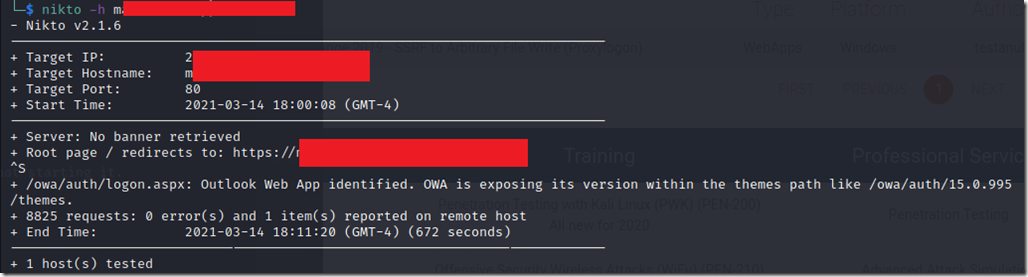
By using Nikto command from Kali Linux I could see what Information could Exchange expose using
The command line is nikto –h mail.domain.com and the result of the scan would be exposing the Server’s name, local IP address, OWA Version, ASP Net platform and version.
Since I have my Exchange Server published via HAProxy 1.8 on Pfsense then I had to tweak HAProxy to strengthen the ciphers, make sure that HSTS is in place and deny the headers that expose the server’s sensitive information.
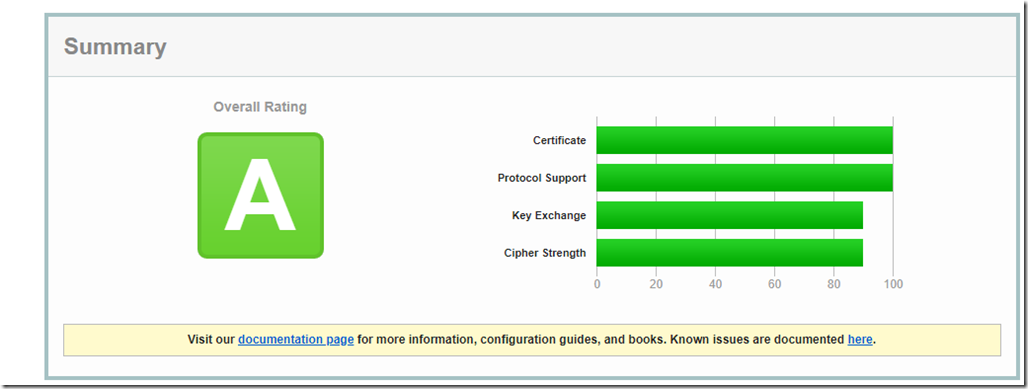
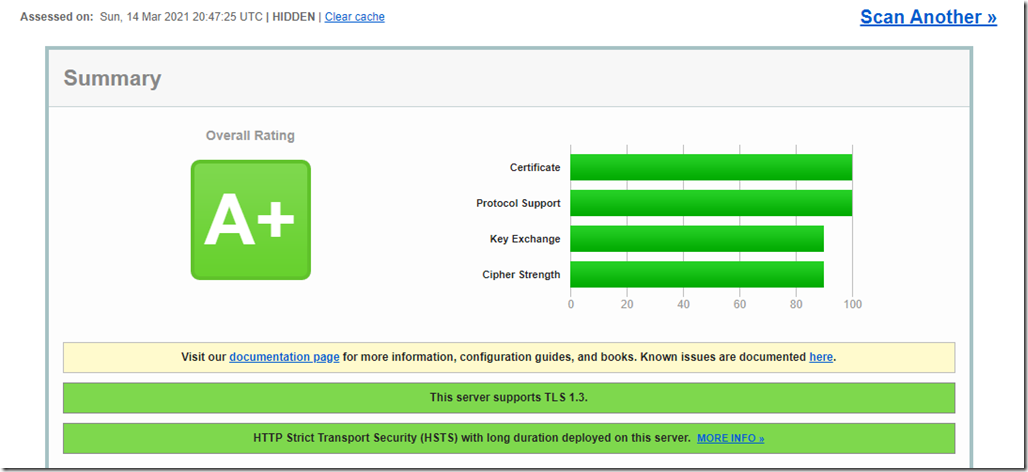
The result is pretty good as it also has affected the server’s score on ssllabs.com
Prior to the tweaking my owa scan result on SSL Labs would get an A
– Pfsense’s HAProxy Settings before
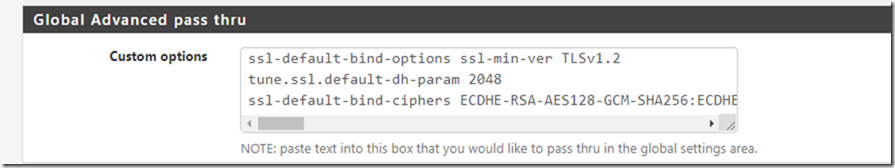
Before upgrading Pfsense to the latest version HAProxy was on 1.6 and the ssl/tls settings were also different as they were setup through the Advanced SSL options on the frontend however, now this is no longer supported and you’ll have to remove that and set it up on the “Global Advanced pass thru” in the General setting page.
ssl-default-bind-options ssl-min-ver TLSv1.2
tune.ssl.default-dh-param 2048
ssl-default-bind-ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!3DES:!MD5:!PSK
Right after you save this, you will still need to change another settings on the Frontend to protect your server’s information from being exposed.
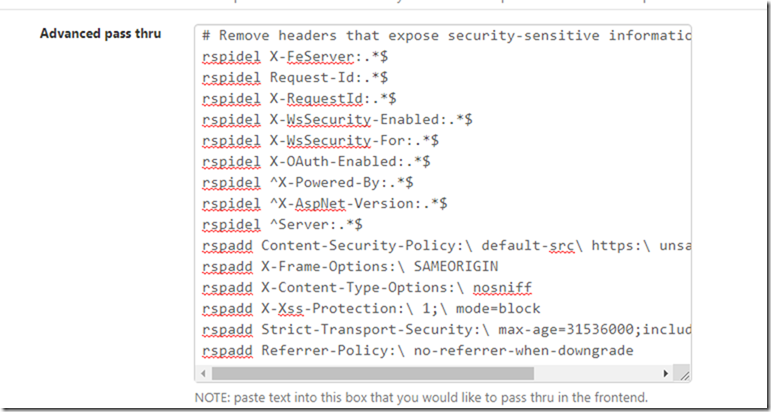
In the HAProxy settings Go to Frontend > Scroll down all the way to “Advanced pass thru” and paste the following:
# Remove headers that expose security-sensitive information.
rspadd X-Frame-Options:\ SAMEORIGIN
rspidel X-FeServer:.*$
rspidel ^Server:.*$
rspidel ^X-Powered-By:.*$
rspidel ^X-AspNet-Version:.*$
rspidel X-WsSecurity-Enabled:.*$
rspidel X-WsSecurity-For:.*$
rspidel X-OAuth-Enabled:.*$
rspadd X-Xss-Protection:\ 1;\ mode=block
rspadd Strict-Transport-Security:\ max-age=31536000;includeSubDomains;preload
rspadd Referrer-Policy:\ no-referrer-when-downgrade
rspidel Request-Id:.*$
rspidel X-RequestId:.*$
rspadd X-Content-Type-Options:\ nosniff
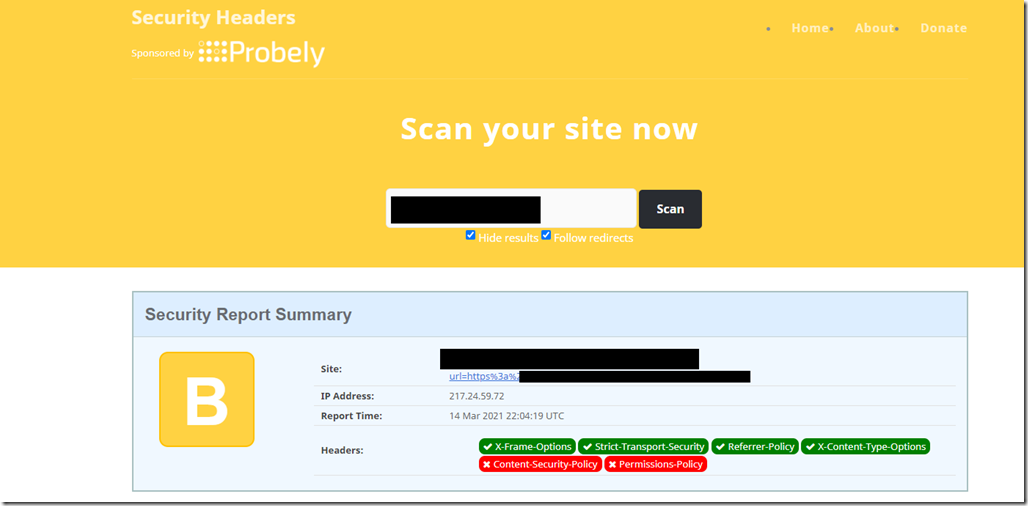
In the below result, I have got almost everything protected well except for the OWA version which can be a bit problematic. In the next article I am going to try and mitigate this so the server can be protected in the expected manner.
– The Result
Now the server is showing a totally different result and the Nikto scan is not revealing anything anymore.
SSLabs
The reason why I got B on security headers is due to the fact that Content-Security-Policy header will malfunction the ECP and OWA Login pages. Permission Policy is new feature and I couldn’t find anything about it on HAProxy.
I hope this helps
Refences:
https://www.haproxy.com/documentation/aloha/12-0/traffic-management/lb-layer7/http-rewrite/
https://www.net7.be/blog/article/xss_csrf_http_security.html